Recently I had problem with my laptop. whenever I shut it down or hibernated, it restarted again. After a few hours searching the internet, I was amazed to see so many people had this problem.
The solutions I found were ranged from changing LAN settings to flash the CMOS, or to restore your windows, and even reinstall the operating system.
The problem they said, was in 'not shutting down properly' which usually happens when you do 'hibernate'. Anyway the solution which I tried and worked for me is to install a software named "RefreshPC, and that's it.
Apparently that software just restores some registry keys to their default values, resets some services to their default settings, and removes some temporary files.
here's the link:
http://www.xp-smoker.com/refreshpc.html
Saturday 17 November 2012
Thursday 15 November 2012
Special Relativity and space travel
The theory of relativity arises from a simple assumption that the speed of light is constant as viewed from any frame of reference. That is, an observer travelling towards a light beam would measure the same speed of light as an observer who is moving away from it.
One of the consequences is that two events can never happen simultaneously. For two stationary observers, an event occuring at time t, will appear to have occured at time t', where t-t' depends on how long light takes to travel to each observer.
So what about moving reference frames?
According to the theory, there is no special reference frame. A person on a plane crusing at a constant speed can never know if he is in motion unless they look out the window. And for all they know, the plane could be stationary and the earth could be moving underneath them. A clock that ticks every second on a plane would also take a second to tick if it was on the ground. However each observer would see a different ticking rate if he looked at the other person's clock:
If the person on the ground makes a measurement of the tick of the clock on the plane, he would first see the clock beginning to tick, but the plane would have moved by the time the tick has finished, so the observer sees a longer tick duration. Time runs slower on the plane.
Another way of looking at this is to imagine two spaceships (A and B) moving away from earth in opposite directions near the speed of light (0.9 C, where C is the speed of light). What would the speed of the spaceship A be as seen from spaceship B? 1.8 C? but we know that faster that C is not possible. The answer is actually 0.996 C. That means that time runs slower in the spaceships relative to eachother, and since distance is speed multiplied by time, the distance between the spaceships also shrinks.
Now to space travel:
If humans ever developed near the speed of light space travel, there would still be a couple of major problems to deal with. The distance to the closest star is about 2 light years. It takes light 2 years to reach it. So from an observer on earth, a spaceship travelling near the speed of light would take slightly more than 2 years to reach it. For the passengers however, time runs slower and depending on how close you are to the speed of light, the time can be reduced indefinitely, but it can never reach zero.
The diameter of the Milky Way galaxy is about 150,000 light years. The closest galaxy, Andromeda, is 2.5 million light years away.
Sending probes it also difficult. We would have to wait 300,000 light years to be able to send and receive a signal across the galaxy, not to mention the signal would have to be very strong. So travelling across the galaxy is like a one-way trip. Don't expect to hear from the passengers soon.
So why would an intelligent race want to travel this far...for resources? unlikely. Intelligent beings capable of building near the speed of light spaceships would be able to manufacture anything they want out of raw matter. Exploration? The cost seems too great. Achieving relativistic speed requires enormous amounts of energy. The most likely scenario is receiving radio signals. But depending on the distances, the signals need to be very strong...such as the signal from pulsars. Pulsars naturally produce powerful radiation at regular intervals. But to be able to control such a system would require lots of energy...perhaps beyond the capabilities of any intelligent being.
But even if we do receive signals, there would be no means of communication within a single human lifespan. The best case scenario would probably be the fact of knowing that other intelligent life exists...nothing more.
Hope you liked the article. Post your questions below. I will be posting a much more detailed (and mathematical) article on relativity soon. Time to take my orange pill now...
U+V1+UVc2
U+V1+UVc2
Monday 12 November 2012
Anti Phishing and anti malware protection In Chrome and Firefox
This is one of my assignment for one of the subjects I had. we were asked to compare one of security features of most recent version of Google Chrome and Firefox. It is not a professional comparison.
References:
Introduction
In this report we compare anti phishing and anti-malware features of the recent versions of two web browsers, Firefox 15, and Chrome 22. We also compare their advantages and disadvantages and their impact on the browsing experience.
In this report we compare anti phishing and anti-malware features of the recent versions of two web browsers, Firefox 15, and Chrome 22. We also compare their advantages and disadvantages and their impact on the browsing experience.
What is phishing?
Phishing and malware
Web Forgery or Phishing is the act of attempting to acquire
information such as usernames, passwords, credit
card details, and sometimes, indirectly, money by masquerading as a trustworthy
entity in an electronic communication.
Communications purporting to be from popular social web sites, auction sites,
online payment processors or IT administrators are commonly used to lure the
unsuspecting public. Phishing emails may contain links to websites that are
infected with malware. Phishing is typically carried out by e-mail spoofing or instant messaging and it often directs users to enter details at a fake
website whose look and feel are almost
identical to the legitimate one. Phishing is an example of social engineering techniques
used to deceive users and
exploits the poor usability of current web security technologies. Attempts to deal with the growing
number of reported phishing incidents include legislation, user
training, public awareness, and technical security measures.
On the other hand, Malware, which is short for malicious software, is software installed on
user’s machine often without user’s knowledge and is designed to disrupt
computer operation, gather sensitive information, or gain access to private
computer systems. It can appear in the form of code, scripts, active content, and other software. Malware
is a general term used to refer to a variety of forms of hostile or intrusive
software. Malware includes computer viruses, worms, Trojan horses, spyware, ad ware, and other malicious programs.
Chrome vs.
Firefox
Chrome is blocking phishing websites or malware in the following way. It periodically retrieves updates of two blacklists, one for phishing and one for malware, and will show users a warning message before users visit a site that is suspected of containing malware or phishing. This service is also made available for use by others via a free public API called "Google Safe Browsing API".
Chrome will typically allocate each tab to fit into its own process to "prevent malware from installing itself" and prevent what happens in one tab from affecting what happens in another. Following the principle of least privilege, each process is stripped of its rights and can compute, but cannot write files or read from sensitive areas, e.g. documents, desktop. For example, malicious software running in one tab is supposed to be unable to sniff credit card numbers entered in another tab, interact with mouse inputs, or tell Windows to "run an executable on start-up" and it will be terminated when the tab is closed. This enforces a simple computer security model whereby there are two levels of multilevel security (user and sandbox) and the sandbox can only respond to communication requests initiated by the user.
Google has also added some new security functionality to new version of Chrome. Every time that the user downloads a file, the browser will compare it against a whitelist of known-good files and publishers. If the file is not in the whitelist, its URL will be transmitted to Google's servers, which will perform an automatic analysis and attempt to guess if the file is malicious based on various factors like the trustworthiness of its source. If the file is deemed a potential risk, the user will receive a warning.
Firefox on the other hand has the same feature and technically does the same things. Firefox gets a fresh update of forgery sites a whopping 48 times a day, so if you try to visit a fraudulent site that’s pretending to be someone you trust; a warning message will stop you before any harm is done.
Firefox’s Phishing and Malware Protection works by checking the sites that you visit against lists of reported phishing and malware sites. There are two times when Firefox checks the phishing and malware protection database and web service. The first is during the regular updates to the lists of reporting phishing and malware sites. The list on your PC is automatically updated every 30 minutes or so when the Phishing and Malware Protection feature is enabled. The second is in the event that you encounter a reported phishing or malware site. Before blocking the site, Firefox requests a double check to ensure that the reported site has not been removed from the list since your last update.
Chrome is blocking phishing websites or malware in the following way. It periodically retrieves updates of two blacklists, one for phishing and one for malware, and will show users a warning message before users visit a site that is suspected of containing malware or phishing. This service is also made available for use by others via a free public API called "Google Safe Browsing API".
Chrome will typically allocate each tab to fit into its own process to "prevent malware from installing itself" and prevent what happens in one tab from affecting what happens in another. Following the principle of least privilege, each process is stripped of its rights and can compute, but cannot write files or read from sensitive areas, e.g. documents, desktop. For example, malicious software running in one tab is supposed to be unable to sniff credit card numbers entered in another tab, interact with mouse inputs, or tell Windows to "run an executable on start-up" and it will be terminated when the tab is closed. This enforces a simple computer security model whereby there are two levels of multilevel security (user and sandbox) and the sandbox can only respond to communication requests initiated by the user.
Google has also added some new security functionality to new version of Chrome. Every time that the user downloads a file, the browser will compare it against a whitelist of known-good files and publishers. If the file is not in the whitelist, its URL will be transmitted to Google's servers, which will perform an automatic analysis and attempt to guess if the file is malicious based on various factors like the trustworthiness of its source. If the file is deemed a potential risk, the user will receive a warning.
Firefox on the other hand has the same feature and technically does the same things. Firefox gets a fresh update of forgery sites a whopping 48 times a day, so if you try to visit a fraudulent site that’s pretending to be someone you trust; a warning message will stop you before any harm is done.
Firefox’s Phishing and Malware Protection works by checking the sites that you visit against lists of reported phishing and malware sites. There are two times when Firefox checks the phishing and malware protection database and web service. The first is during the regular updates to the lists of reporting phishing and malware sites. The list on your PC is automatically updated every 30 minutes or so when the Phishing and Malware Protection feature is enabled. The second is in the event that you encounter a reported phishing or malware site. Before blocking the site, Firefox requests a double check to ensure that the reported site has not been removed from the list since your last update.
Advantage and disadvantage
Since Google has indexed most of the website in the internet it is much easier for Chrome to have the phishing websites list to be very up to date. Another big advantage is that, whenever a phishing website is running on one tab, it does not effect on other tabs or operating system itself, because every tab is running in different so called jail. Firefox, however, uses Google service called “Google Safe Browsing API”, which is big disadvantage since it uses other rival browser creator technique.
The disadvantage of the Chrome’s way of dealing with phishing and malware protection is user concern of privacy. Every time a file is being downloaded chrome send the file and the website information to Google to check against its database of safe websites and sends back the information to the browser, which some users do not like that who are concern about their privacy.
The advantage of Firefox over chrome is that it does not send any user’s information back to anywhere like Chrome does, so users do not need to be worried about someone checking their files or information by sending back somewhere over internet.
Since Google has indexed most of the website in the internet it is much easier for Chrome to have the phishing websites list to be very up to date. Another big advantage is that, whenever a phishing website is running on one tab, it does not effect on other tabs or operating system itself, because every tab is running in different so called jail. Firefox, however, uses Google service called “Google Safe Browsing API”, which is big disadvantage since it uses other rival browser creator technique.
The disadvantage of the Chrome’s way of dealing with phishing and malware protection is user concern of privacy. Every time a file is being downloaded chrome send the file and the website information to Google to check against its database of safe websites and sends back the information to the browser, which some users do not like that who are concern about their privacy.
The advantage of Firefox over chrome is that it does not send any user’s information back to anywhere like Chrome does, so users do not need to be worried about someone checking their files or information by sending back somewhere over internet.
Conclusion
Overall both browsers are doing the same thing to prevent phishing and protect users from malware files and phishing websites, however, Chrome has been proved that is doing slightly better than Firefox in protecting users from this security threat.
Overall both browsers are doing the same thing to prevent phishing and protect users from malware files and phishing websites, however, Chrome has been proved that is doing slightly better than Firefox in protecting users from this security threat.
- http://en.wikipedia.org/wiki/Features_of_Firefox#Security
- http://en.wikipedia.org/wiki/Malware
- http://en.wikipedia.org/wiki/Phishing
- https://www.google.com/intl/en/chrome/browser/features.html#security
- http://arstechnica.com/business/2012/02/chrome-17-released-will-preload-autocompleted-urls-as-you-type/
- http://www.mozilla.org/en-US/firefox/features/
- http://en.flossmanuals.net/firefox/ch036_firefox-security-features/
Set Operations using ArrayList
I implemented set operations using only ArrayList and Iterator, which are part of java.util class. Java has its own Set data structure though.
The challenge for this assignment was to use only ArrayList and Iterator. I was trying to implement a BinaryTree data structure based on ArrayList and then implement my set operations on top of that. The worst case running time using ArrayList for most of the operations is O(n^2), while by using BinaryTree they can be done in O(nlog n), worst case. Here I put my code using only ArrayList features. I will make another post about my BinaryTree implementation using ArrayList.
Set class:
Here is the MySet class which implements the Set class:
There was extra mark for efficient running time which I think I won't get any, since the worst case running time for my implementation is O(n^2).
My code passed all the on line tests, however if anybody finds any problem, please leave a comment.
Leo the Pamador
The challenge for this assignment was to use only ArrayList and Iterator. I was trying to implement a BinaryTree data structure based on ArrayList and then implement my set operations on top of that. The worst case running time using ArrayList for most of the operations is O(n^2), while by using BinaryTree they can be done in O(nlog n), worst case. Here I put my code using only ArrayList features. I will make another post about my BinaryTree implementation using ArrayList.
Set class:
Here is the MySet class which implements the Set class:
There was extra mark for efficient running time which I think I won't get any, since the worst case running time for my implementation is O(n^2).
My code passed all the on line tests, however if anybody finds any problem, please leave a comment.
Leo the Pamador
Sunday 14 October 2012
Saturday 13 October 2012
1 trillion frames per second camera
I came across this cool video on youtube. This camera is so fast, it can take a video of a travelling light beam. You can also use it as a type of optical radar to look around corners:
Wednesday 10 October 2012
2012 Nobel Prize in Physics announced:
The Nobel Prize in Physics 2012 was awarded jointly to Serge Haroche and David J. Wineland "for ground-breaking experimental methods that enable measuring and manipulation of individual quantum systems".
"The Nobel Laureates have opened the door to a new era of experimentation with quantum physics by demonstrating the direct observation of individual quantum particles without destroying them," commented the academy in a statement.
Haroche and Wineland have independently invented and developed methods for measuring and manipulating individual particles through 1970s to 1990s while preserving their quantum-mechanical nature in ways that were previously thought unattainable.
The two scientists and their research groups have managed to measure and control very fragile quantum states which were previously thought inaccessible for direct observation, according to the academy.
"Their ground-breaking methods have enabled this field of research to take the very first steps towards building a new type of super fast computer based on quantum physics" (see Quantum computer) and "change our everyday lives in this century in the same radical way as the classical computer did in the last century," the statement added.
This years's cash award is 8 million Swedish kronor (about 1 million U.S. dollars).
for more info visit: http://www.nobelprize.org/nobel_prizes/physics/laureates/2012/#
"The Nobel Laureates have opened the door to a new era of experimentation with quantum physics by demonstrating the direct observation of individual quantum particles without destroying them," commented the academy in a statement.
Haroche and Wineland have independently invented and developed methods for measuring and manipulating individual particles through 1970s to 1990s while preserving their quantum-mechanical nature in ways that were previously thought unattainable.
The two scientists and their research groups have managed to measure and control very fragile quantum states which were previously thought inaccessible for direct observation, according to the academy.
"Their ground-breaking methods have enabled this field of research to take the very first steps towards building a new type of super fast computer based on quantum physics" (see Quantum computer) and "change our everyday lives in this century in the same radical way as the classical computer did in the last century," the statement added.
This years's cash award is 8 million Swedish kronor (about 1 million U.S. dollars).
for more info visit: http://www.nobelprize.org/nobel_prizes/physics/laureates/2012/#
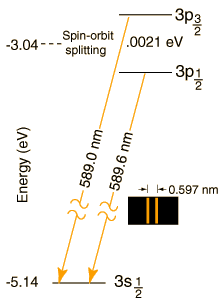
Sodium doublet at 589 nm
The 589.0 nm spectral line of the sodium yellow doublet is a transition from the 2P3/2
excited states to the 2S1/2 ground state of the sodium atom.
Energy level diagram showing how the two energy levels are split in the
presence of a weak magnetic field:
The 3P3/2 level is split because of L-S coupling.
The selection rules for this transition are:
Δ l = ±1
Δ j = ±1, 0
For the transition from 3P3/2 ===> 3S1/2, Δ l = +1 (since S = 0 and P = 1)
and Δ j = 0 for the 3P1/2 ===> 3S1/2 and +1 for the 3P3/2 ==> 3S1/2 transition. (j = s+l and is given by the subscript).
Therefore the transitions satisfy the selection rules.
excited states to the 2S1/2 ground state of the sodium atom.
Energy level diagram showing how the two energy levels are split in the
presence of a weak magnetic field:
The 3P3/2 level is split because of L-S coupling.
The selection rules for this transition are:
Δ l = ±1
Δ j = ±1, 0
For the transition from 3P3/2 ===> 3S1/2, Δ l = +1 (since S = 0 and P = 1)
and Δ j = 0 for the 3P1/2 ===> 3S1/2 and +1 for the 3P3/2 ==> 3S1/2 transition. (j = s+l and is given by the subscript).
Therefore the transitions satisfy the selection rules.
Free electron energy levels
An unpaired electron in a molecular radical can be considered to be an effectively free electron. A free electron in a magnetic field has two energy levels due to the two possible orientations of
its spin, and hence of its magnetic moment, with respect to the magnetic field.
The energies of the levels are given by:
E = -μs.B = +- μB.B , where
If an oscillator of frequency 50 MHz is used for an ESR experiment, we can easily calculate the magnetic field required to achieve a transition:
hf = 2μB.B, rearranging this gives us: B = hf*meC/(e*hbar) = 2*f*pi*meC/e
using f = 50 MHz, we get get B = 1.78 mT
Please leave a comment on how you found this page! thanks
its spin, and hence of its magnetic moment, with respect to the magnetic field.
The energies of the levels are given by:
E = -μs.B = +- μB.B , where
If an oscillator of frequency 50 MHz is used for an ESR experiment, we can easily calculate the magnetic field required to achieve a transition:
hf = 2μB.B, rearranging this gives us: B = hf*meC/(e*hbar) = 2*f*pi*meC/e
using f = 50 MHz, we get get B = 1.78 mT
Please leave a comment on how you found this page! thanks
Monday 17 September 2012
Dr Michio Kaku talks about physics:
Tuesday 11 September 2012
Eye of the Tiger
This is a great inspiring song. It's the theme song for Rockey III movie.
It's from Survivor group.
Here's the video. I hope you enjoy it.
Here's some lines from the song:
...So many times, it happens too fast
You trade your passion for glory
Don't lose your grip on the dreams of the past
You must fight just to keep them alive
It's the eye of the tiger
It's the thrill of the fight
Risin' up to the challenge
Of our rival
And the last known survivor....
It's from Survivor group.
Here's the video. I hope you enjoy it.
...So many times, it happens too fast
You trade your passion for glory
Don't lose your grip on the dreams of the past
You must fight just to keep them alive
It's the eye of the tiger
It's the thrill of the fight
Risin' up to the challenge
Of our rival
And the last known survivor....
Friday 7 September 2012
Free .Net Programming ebooks
We have a collection of ebooks in programming, mostly .Net, and we are happy to send to anybody who wants a copy of their desired topic for free.
You only need to leave a comment with your book name, and email address and we mail it to you.
this is free, it doesn't have anything to do with on line marketing or stuff.
we couldn't come up with any other solution to publish these ebooks,
and we don't have any website whatsoever.
we don't use your email address for any other matters, which we are not really interested in your email for any reason.
regards
You only need to leave a comment with your book name, and email address and we mail it to you.
this is free, it doesn't have anything to do with on line marketing or stuff.
we couldn't come up with any other solution to publish these ebooks,
and we don't have any website whatsoever.
we don't use your email address for any other matters, which we are not really interested in your email for any reason.
regards
Thursday 6 September 2012
How to install Gnome shell in Ubuntu 12?
Steps are so simple:
go to 'Ubuntu Software Centre' and search for 'Gnome Shell', our desired shell should be first or second one in the returned list. its name simply is 'Gnome Shell'. click it and then click 'Install'
It takes a while to finish downloading and installing. after installation finishes just log out the system and then log in to the system.
this time when you want to log in there is extra option next to your user name where you can choose your newly installed shell, and that's it.
you can also install Gnome shell using terminal by following command:
sudo apt-get install gnome-shell
There are other shells and extension as well.
go to 'Ubuntu Software Centre' and search for 'Gnome Shell', our desired shell should be first or second one in the returned list. its name simply is 'Gnome Shell'. click it and then click 'Install'
It takes a while to finish downloading and installing. after installation finishes just log out the system and then log in to the system.
this time when you want to log in there is extra option next to your user name where you can choose your newly installed shell, and that's it.
you can also install Gnome shell using terminal by following command:
sudo apt-get install gnome-shell
There are other shells and extension as well.
Monday 3 September 2012
Removing your email account in Thunderbird
When you set up your email account with Thunderbird all your mails can be seen by other people who have access to the system. for synchronization, it needs your password but still your old emails are on the system. to remove your account from Thunderbird:
you can go to menu 'Edit' > 'Account Settings' then it asks you for your email password, after authentication, you have an option at the button of 'Account Settings' which is "Account Action' click it and then you can choose to remove your email account form Thunderbird.
Sunday 2 September 2012
Reflection of a Binary Tree
Reflection of binary tree means if you have a binary tree like following:
a a
/ \ becomes like this / \
b c c b
/ \ / \ / \ / \
d e f g g f e d
There are 2 approaches to this problem 1- using stack 2- recursively swap sub trees
I explain both and give Java code for second approach.
1.Using Stack
If you have recursion, you almost always can do the same job using stack. steps to produce reflection of a binary tree is:
1- Push the node in the stack
2- Pop the node from stack and if it has childes swap them
3- Push the left child and right child after swap
4- do theses steps until stack becomes empty which means you visited all nodes
example:
2- Recursive method
1-if root is empty return
2- call reflect for left sub tree
3- call reflect for right sub tree
4- swap left and right sub trees using temp variable...temp is the same type of node.
Java code:
Testing:
To test operation on binary tree, the best approach in my opinion is to use Graphvis website which shows you visual output based on your input. you can write a method to traverse your tree after and before reflection and generate a Graphvis dot file or its accepted input data, then you can use Graphvis to see the output is what it is supposed to be.
I give a Java code for generating dot output to use in Graphvis .
output is in String format, however you can write the output to a .dot file and then load it on Graphvis website.
Java code for generating Graphvis .dot data:
p.s: When using this generator you should add the following line before the actual data inside the curly braces to give you right visual output: graph [ordering="out"];
p.s.s: You can also use queue instead of stack.
a a
/ \ becomes like this / \
b c c b
/ \ / \ / \ / \
d e f g g f e d
There are 2 approaches to this problem 1- using stack 2- recursively swap sub trees
I explain both and give Java code for second approach.
1.Using Stack
If you have recursion, you almost always can do the same job using stack. steps to produce reflection of a binary tree is:
1- Push the node in the stack
2- Pop the node from stack and if it has childes swap them
3- Push the left child and right child after swap
4- do theses steps until stack becomes empty which means you visited all nodes
example:
stack: push 'a'
pop 'a' then swap 'b' and 'c'.
stack: push 'c'. push 'b'.
pop 'b' then swap it childes, 'e' and 'd'
stack: push 'd'. push 'e'
pop 'e' which doesn't have children so return.
pop 'd' which doesn't have children so return.
stack : only contains 'c' now
continue...
pop 'c' and swap its children.
stack: push 'g'. push 'f''
pop 'f'' which doesn't have children so return.
pop 'g' which doesn't have children so return.
stack is empty now so finish.
2- Recursive method
For operations on binary tree most of the times using recursion is a good idea.
with recursion, reflection happens in place which means the original tree replace with reflected tree.recursion is shorter than first method.
imagine you have method called reflect(Node<E> node)
which accept Node<E> of the binary tree. we call this method in our caller method with root of binary tree.
steps are:
2- call reflect for left sub tree
3- call reflect for right sub tree
4- swap left and right sub trees using temp variable...temp is the same type of node.
Java code:
Testing:
To test operation on binary tree, the best approach in my opinion is to use Graphvis website which shows you visual output based on your input. you can write a method to traverse your tree after and before reflection and generate a Graphvis dot file or its accepted input data, then you can use Graphvis to see the output is what it is supposed to be.
I give a Java code for generating dot output to use in Graphvis .
output is in String format, however you can write the output to a .dot file and then load it on Graphvis website.
Java code for generating Graphvis .dot data:
p.s: When using this generator you should add the following line before the actual data inside the curly braces to give you right visual output: graph [ordering="out"];
p.s.s: You can also use queue instead of stack.
Wednesday 22 August 2012
Life is not what we want!
Samia Yusof who ran along the hell.
Do you think she made a stupid decision by trying to go to the Europe with a small boat?
The title of this news is enough tragic : An Olympic athlete died, trying immigrate to the so-called rich north.
What happened to her after Beijing 2008 which forced her to do such thing?
How she decided to get in that small boat? To achieve her dream living in the UK? to earn money and help her family?
Samia appeared in the media almost 4 years ago because being the last one to pass the final line in 200m.
Everybody applaud when she passed the line, and she was so excited just like a winner!
"I`m so proud to be here shaking Somalia`s flag and being with the best of the world" she said.
she was 17 then.
Beijing journey was a golden span in her life; almost all girls get raped every day in Somalia by the fundamentalists militia, who wanted her be covered staying at home. she had been suffered many of those penalties, most them from the Government of the country who she was proud to shake its flag there!
Search and read the rest if you see it is interesting to know what happened to her. who cares I think they don't have oil there!
Look at this video. almost all of them has a thicker arms than her leg. :(
Do you think she made a stupid decision by trying to go to the Europe with a small boat?
The title of this news is enough tragic : An Olympic athlete died, trying immigrate to the so-called rich north.
What happened to her after Beijing 2008 which forced her to do such thing?
How she decided to get in that small boat? To achieve her dream living in the UK? to earn money and help her family?
Samia appeared in the media almost 4 years ago because being the last one to pass the final line in 200m.
Everybody applaud when she passed the line, and she was so excited just like a winner!
"I`m so proud to be here shaking Somalia`s flag and being with the best of the world" she said.
she was 17 then.
Beijing journey was a golden span in her life; almost all girls get raped every day in Somalia by the fundamentalists militia, who wanted her be covered staying at home. she had been suffered many of those penalties, most them from the Government of the country who she was proud to shake its flag there!
Search and read the rest if you see it is interesting to know what happened to her. who cares I think they don't have oil there!
Look at this video. almost all of them has a thicker arms than her leg. :(
Saturday 18 August 2012
You wanted to be successful here's a great video..watch it
I watched this video couple of times in a row.it' really encouraging.
here's a good quote from this video
...Don't try to quit! you're already in pain, you're already hurt, get a reward from it...
here's a good quote from this video
...Don't try to quit! you're already in pain, you're already hurt, get a reward from it...
Friday 17 August 2012
Installing VMware tools on Ubuntu machine
Steps are so simple:
First you need to mount VMware Tools CD image. Turn on your virtual machine then log in to your machine using your administrator account. then go to 'VM' > 'Install VMware Tools...'.
then the file you're looking for is mounted in your CD/DVD ROM. name of the file is something like "VMwareTools-8.8.0-471268.tar.gz" , numbers might be different based on your version of VMware.
right click on it and copy it on your desktop and then select "Extract here".
After extraction; it creates a new folder name "vmware-tools-distrib"
then you need to run the Terminal inside the Ubuntu which is something like Microsoft command propmt
I'm using Ubuntu 12, so click on "Dash Home" and "Terminal" should be there; if not type "Terminal" in search box and find it. run the Terminal.
you need to go to the desktop where the VMware tools are located.
command is:
cd home/username/Desktop/vmware-tools-distrib
where username is your username you log in to Ubuntu. then run following command:
sudo ./vmware-install.pl -d
-d parametter doing that automatically, if you don't like that, remove it and answer the question as prompted.
enter your password if you are asked.
restart your machine and your done.
remember commands in Ubuntu is case-sensative, which means "desktop" is different than "Desktop"
here's another website which has more detail about the process and cover different versions.
http://kb.vmware.com/selfservice/microsites/search.do?cmd=displayKC&externalId=1022525
First you need to mount VMware Tools CD image. Turn on your virtual machine then log in to your machine using your administrator account. then go to 'VM' > 'Install VMware Tools...'.
then the file you're looking for is mounted in your CD/DVD ROM. name of the file is something like "VMwareTools-8.8.0-471268.tar.gz" , numbers might be different based on your version of VMware.
right click on it and copy it on your desktop and then select "Extract here".
After extraction; it creates a new folder name "vmware-tools-distrib"
then you need to run the Terminal inside the Ubuntu which is something like Microsoft command propmt
I'm using Ubuntu 12, so click on "Dash Home" and "Terminal" should be there; if not type "Terminal" in search box and find it. run the Terminal.
you need to go to the desktop where the VMware tools are located.
command is:
cd home/username/Desktop/vmware-tools-distrib
where username is your username you log in to Ubuntu. then run following command:
sudo ./vmware-install.pl -d
-d parametter doing that automatically, if you don't like that, remove it and answer the question as prompted.
enter your password if you are asked.
restart your machine and your done.
remember commands in Ubuntu is case-sensative, which means "desktop" is different than "Desktop"
here's another website which has more detail about the process and cover different versions.
http://kb.vmware.com/selfservice/microsites/search.do?cmd=displayKC&externalId=1022525
Wednesday 15 August 2012
Great videos about Greedy Algorithm
I have Algorithm and Complexity this semester and found good videos from Berkeley university on youtube.
This Lecturer, Professor Gusfield, explains the concept really well..better than my lecturer at least.
This Lecturer, Professor Gusfield, explains the concept really well..better than my lecturer at least.
Education should be free for all
I think education should be free for all students or whoever wants to study. Students should not pay for their books, or tuition fees or whatsoever.
Government must support the students. I have to pay $700 for just books which I'm studying in this semester.
imagine this amount of money for other semesters and the pressure and anxiety.
Thanks technology we have internet these days, you can have access to lots of materials or videos.
the profit is far more greater than any loss or expenses due to week students.
Government must support the students. I have to pay $700 for just books which I'm studying in this semester.
imagine this amount of money for other semesters and the pressure and anxiety.
Thanks technology we have internet these days, you can have access to lots of materials or videos.
the profit is far more greater than any loss or expenses due to week students.
Friday 3 August 2012
Reading CHM files on IPad
To open CHM files on IPad, the best option is CHMate Lite app
You can either transfer your file to CHMate using your laptop or desktop or if you have your file in GoodReader then it is really easy, follow these steps:
1-Click manage files in GoodReader
2-Select your file and choose "Open In"
3- Then CHMate popes up , select it and you're done.
You can either transfer your file to CHMate using your laptop or desktop or if you have your file in GoodReader then it is really easy, follow these steps:
1-Click manage files in GoodReader
2-Select your file and choose "Open In"
3- Then CHMate popes up , select it and you're done.
Welcome Post
This is the first post of my first blog on my first try to do this kind of stuff.I almost write everything which I think are either useful or interesting to anybody out there.
good luck for me
good luck for me
Subscribe to:
Posts (Atom)